22
May
2023
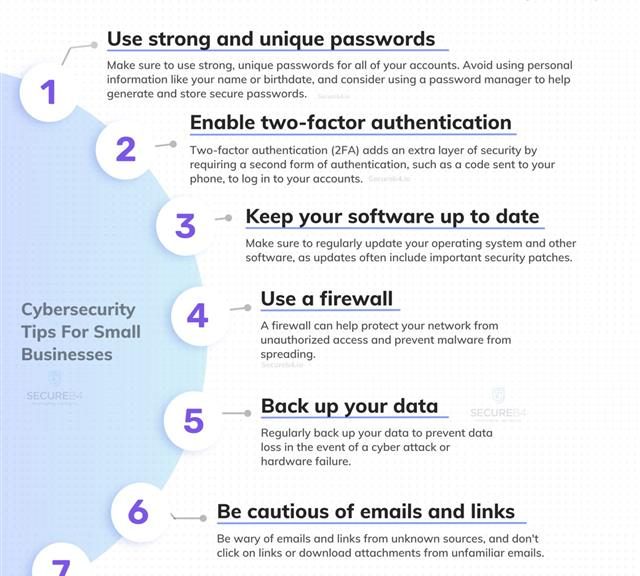
In the digital world, small doesn’t mean safe. Cyber threats don’t discriminate based on the size of your business. A cyber attack can be a nightmare for small businesses, but fear not! We’ve got 7 essential cybersecurity tips that can help you fortify your defenses! 🛡️💻
1️⃣ Use Strong and Unique Passwords: Your password is like a digital key to your business. Make it unique, complex, and hard to guess. Consider using a password manager to help maintain strong, distinct passwords for each account.
2️⃣ Enable Two-Factor Authentication (2FA): This adds an extra layer of security, requiring more than just a password to access your account. It’s like a double lock for your digital doors.
3️⃣ Keep Your Software Up-to-Date: Regular updates patch vulnerabilities that cybercriminals could exploit. It’s like a health check-up for your systems.
4️⃣ Use a Firewall: A firewall monitors and controls the incoming and outgoing network traffic based on your security policies. Think of it as your digital security guard.
5️⃣ Back Up Your Data: Regularly back up critical business data. In case of a cyber attack, it’s like having an insurance policy for your data.
6️⃣ Be Cautious of Emails and Links: Not every email and link is what it seems. Be wary of phishing attempts where cybercriminals may pose as trusted entities. Always double-check before you click!
7️⃣ Educate Your Employees: Your employees are the frontline defenders against cyber threats. Train them to recognize and respond appropriately to potential threats. Knowledge is power, after all!
Remember, cybersecurity isn’t a one-time event but a continuous process. Stay vigilant, stay updated, and let’s build a safer digital environment for our businesses! 💪🔒🌐