
Top 7 Types of Cyber Crimes
Unmasking the Digital Shadows: Cyber crime, the unseen threat that lurks in the realm of computers and networks, striking individuals, organizations, and governments alike.Please read the full articles here.

Unmasking the Digital Shadows: Cyber crime, the unseen threat that lurks in the realm of computers and networks, striking individuals, organizations, and governments alike.Please read the full articles here.

This helpful guide will teach you the basics of protecting your business from cyber attacks. Follow these tips to keep your files, devices, and wireless network secure. The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk...Continue reading TrickBot Malware
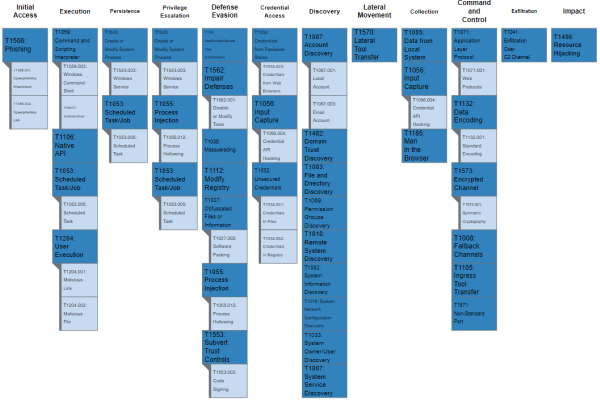
This Joint Cybersecurity Advisory uses the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK®) framework, Version 8. See the ATT&CK for Enterprise for all referenced threat actor tactics and techniques. The Cybersecurity and Infrastructure Security Agency (CISA) and Federal Bureau … Continue reading TrickBot Malware

Prevent ransomware incursions and defend against ransomware attacks. Sophisticated ransomware attacks are on the rise and evolving quickly. Executives want reassurance but are not ready to write a blank check. ... Continue reading Azure Sentinel Design

CISA, the Federal Bureau of Investigation (FBI), the National Security Agency (NSA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) published an updated version of the #StopRansomware Guide, as ransomware actors have accelerated their tactics and techniques since its … Continue reading Stop Ransomware Guide
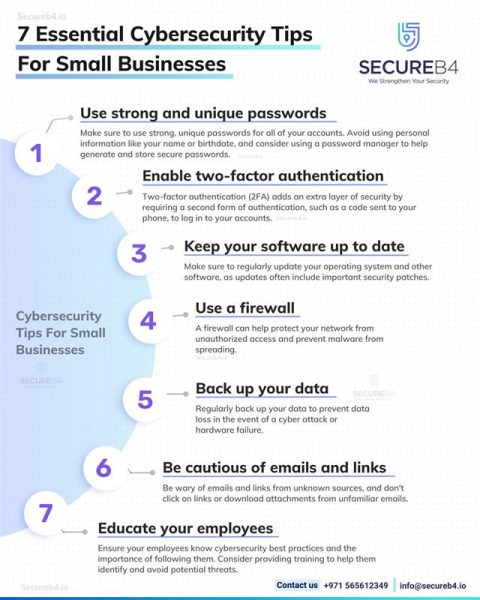
In the digital world, small doesn’t mean safe. Cyber threats don’t discriminate based on the size of your business. A cyber attack can be a nightmare for small businesses, but fear not! We’ve got 7 essential cybersecurity tips that can … Continue reading 7 Essential Cyber Security Tips For Small Business

Studies show that up to 20 percent of all cybersecurity breaches are ransomware attacks. While this form of malware can be complex and have major impacts to organizations, preparing for these attacks often just requires a focus on the basics … Continue reading Ransomware Preparedness Checklist

Modern-day cybersecurity threats require close monitoring and effective response. However, as data expands from on-premises to the cloud – or somewhere in between – new blind spots are emerging. Read or download the full article :